Dreamhack Wargame Web Exercises Stage 3
Dreamhack Wargame Web Stage 3 Writeups
Overview
Dreamhack is an online Korean collection of challenges from a variety of challenges. I am focusing on the web challenges and am now at stage 3.
Challenges
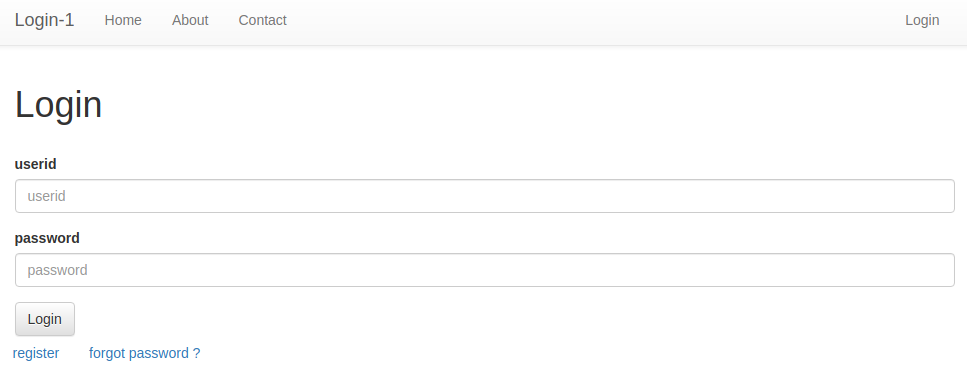
Login 1
This challenge is about gaining access to an admin account to gain the flag. It involves exploiting a race condition to change the password of the admin user. We are shown the login function as well as register and forgot password functions. At this stage the attack vector could be in any one of these so we need to look at the code.
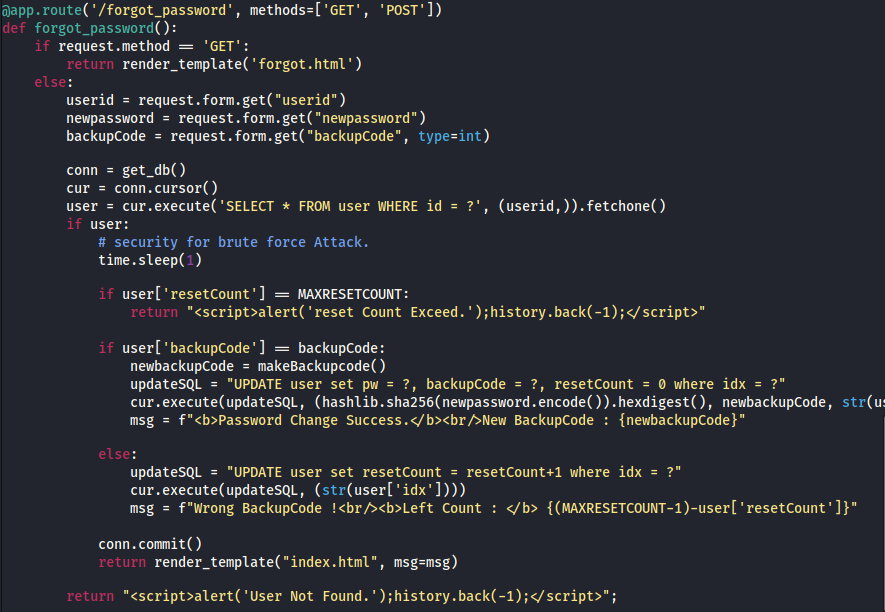
The python application includes code for all 3 functions but we will be focusing on forgot_password. There are a few points of interest here. Firstly, we can see that for each request the program will sleep for 1 second. This is what will later allow us to exploit it. We also see that you can only submit 5 forgot_password requests before being locked out of it. This is what needs to be exploited. We essentially have 1 second from the time the first request goes out to submit as many requests as possible to excede the 5 request limit. If each of those contains a different backup code then we can bruteforce all of them. There are only 100 possible backup codes so we need a script to send 100 requests.
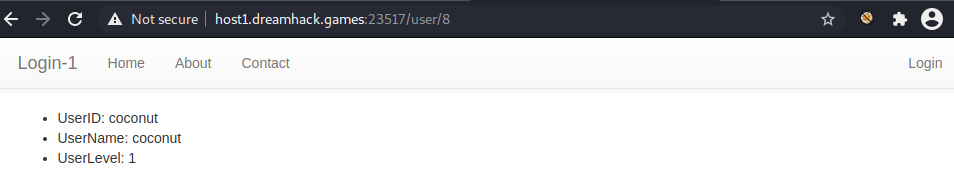
I was originally planning on using admin as the userid. When testing it though it was not a valid userid. Looking at the code once more I noticed the user/idx path. This allows you to search for information on users based on their id number instead of the name. Starting at 0 I found 17 accounts including the one I made as a test. Each one gave 3 lines of information. The UserID associated with it, the UserName associated with it and the UserLevel. The userlevel is either 1 or 0 where 1 is an admin account and 0 is a guest account. I found the users coconut, lemon, potato, peach and orange all of which were admin accounts. The following is an example output for the user coconut.
Having found valid admin accounts we now need to make the script to exploit this. The script to do this is simple and makes use of the requests and threading libraries. We specify the URL and parameters for the form and send each request in its own thread.
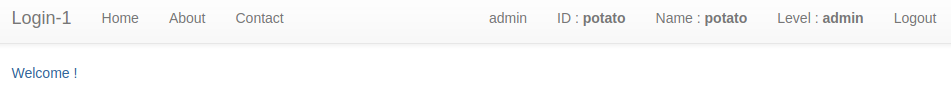
When we do this the password for that user should have changed and we can login with it. When we log in we are brought to this admin login page which confirms that we have gained access.
Finally, to get the flag we can click the admin link at the top and the flag is output on a plaintext document.
DH{4b308b526834909157a73567075c9ab7}